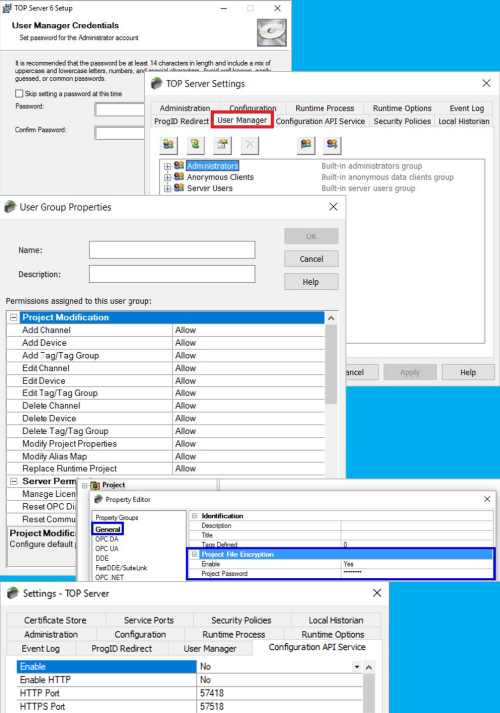
Security is a primary focus in TOP Server
The TOP Server's built-in User Manager and other security features will help you prevent unauthorized changes to your configuration and other cyber threats. From V6.5 forward, users are prompted to enable User Manager as part of the installation by choosing an Administrator account password. From V7 forward, user access to TOP Server configuration and the OPC UA Server interface can leverage your Active Directory infrastructure for robust, centralized security.
The TOP Server Secure Deployment Considerations Guide is a good resource for ensuring your TOP Server is following best practices for maximum security. The TOP Server Out-of-the-Box Security Features technical blog also provides a deep dive.